Acquiring Memory in Digital Forensics: Vendor Tools vs. Custom Solutions
Background: Before analyzing volatility memory , there is a crucial preparatory stage: defining the tool scope for memory acquisition. In this phase, there are two primary approaches—either implementing custom in-house tools or relying on pre-existing vendor/open-source solutions.
Memory Acquisition Challenges for In-House Solutions:
Before diving deep into the development of the acquisition tool, it is essential to understand the modes in the OS (Windows): Kernel mode and User mode. Kernel mode deals with hardware and its drivers. User mode is the application level, which interacts with kernel mode through API interfaces in correlation.
Without proper implementation of drivers, which need to be loaded into the kernel, it is not possible to capture the entire memory.
- Each driver needs to be properly checked to avoid causing BSOD (Blue Screen of Death) and other issues.
- Cross-platform testing
- Human and Process Resource
Memory Acquisition Challenges for Vendor/OpenSource Solutions:
- Price
- Danger of Supply Chain Attack
- Cross-platform testing
High Level Map How Volatility Acquire Work:
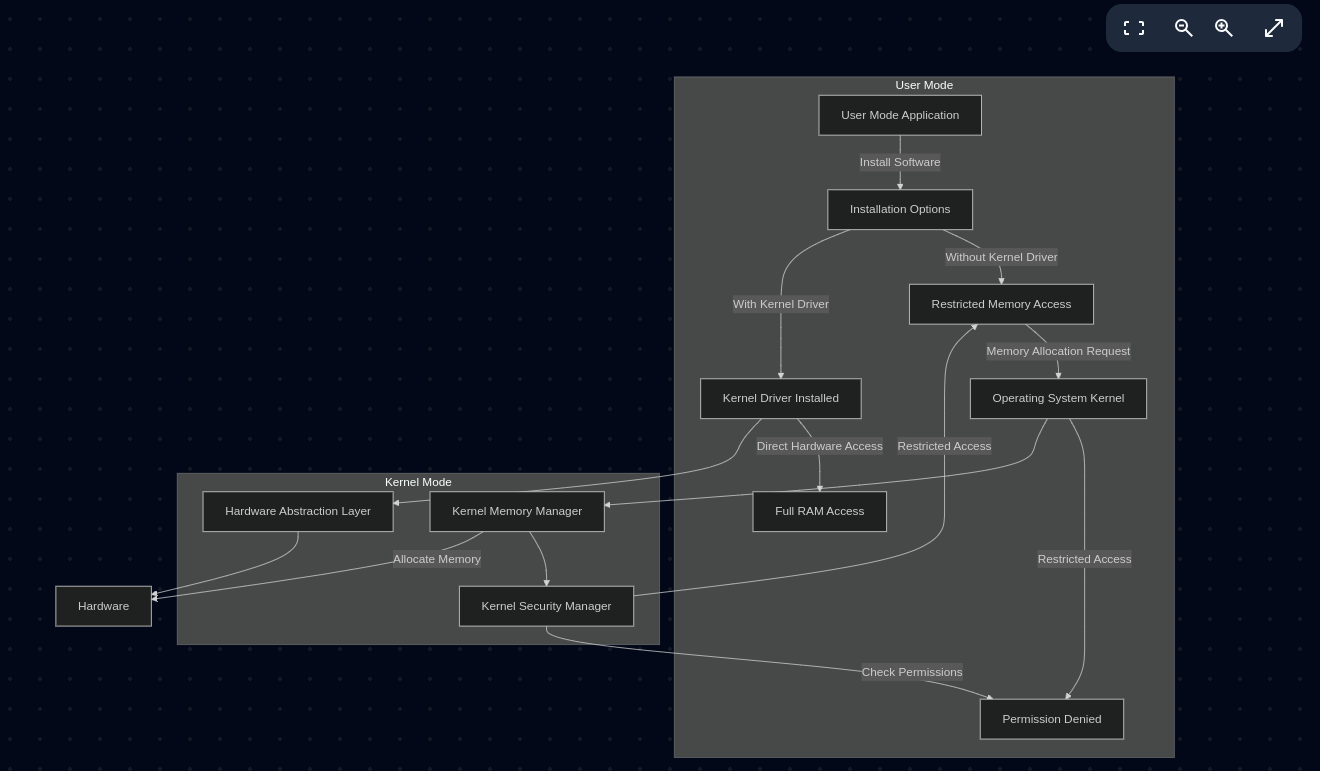
Kernel API lists to deal with memory:
MmMapMemoryDumpMdlEx
mmmaplockedpagesspecifycache
MmMapIoSpace
ZwMapViewOfSection
Conclusion:
In-house solutions for memory acquisition offer the advantage of customization and control over the implementation, which allows for the tailoring of tools to specific needs and environments. However, these solutions come with significant challenges, including the need for thorough driver implementation and testing to avoid system crashes and ensure compatibility across different platforms.
On the other hand, vendor/open-source solutions may provide a quicker and potentially more reliable setup but at the cost of higher expenses and the risk of supply chain attacks. Additionally, these solutions still require rigorous cross-platform testing to ensure they work seamlessly across various systems.
Deciding between these approaches depends on the specific requirements, resources, and risk tolerance of the organization.
Happy Hunt ! Jok3r
