Researching CVE-2025-14847 (Mongo memory leak): Defensive Strategies and Detection Techniques
Background: A few days ago, there was a notification about a memory leak issue (CVE) affecting MongoDB. Shortly after, a proof-of-concept (POC) was released on one of the version control channels. As a result, I began researching the CVE to understand the metrics that can be used to detect exploitation of this vulnerability against our infrastructure.
Research result: Because nowadays many infrastructures rely on virtualization systems, the research has focused on that aspect. Instead of analyzing process call traces in detail, our study examines system behavior from the standpoint of network and CPU usage. Since this CVE primarily targets memory, the attacker faces two layers of defense: first, they must find an exposed MongoDB instance and bypass its rate limits; then, they attempt to exfiltrate memory and find sensitive data.
Research condition:
We measured the performance of a Docker container’s CPU, then attempted to run the exploit to exfiltrate memory. As a result, it was observed that CPU usage remained low until the actual exploitation occurred.
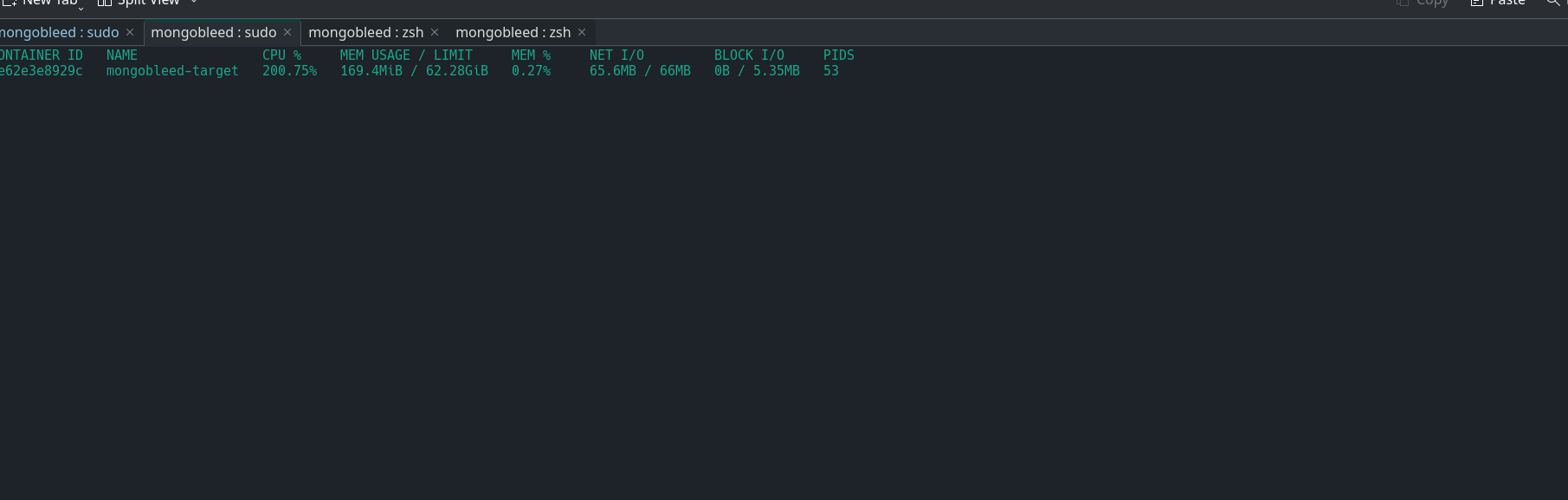
During exploitation CPU usage was increased with about 30%
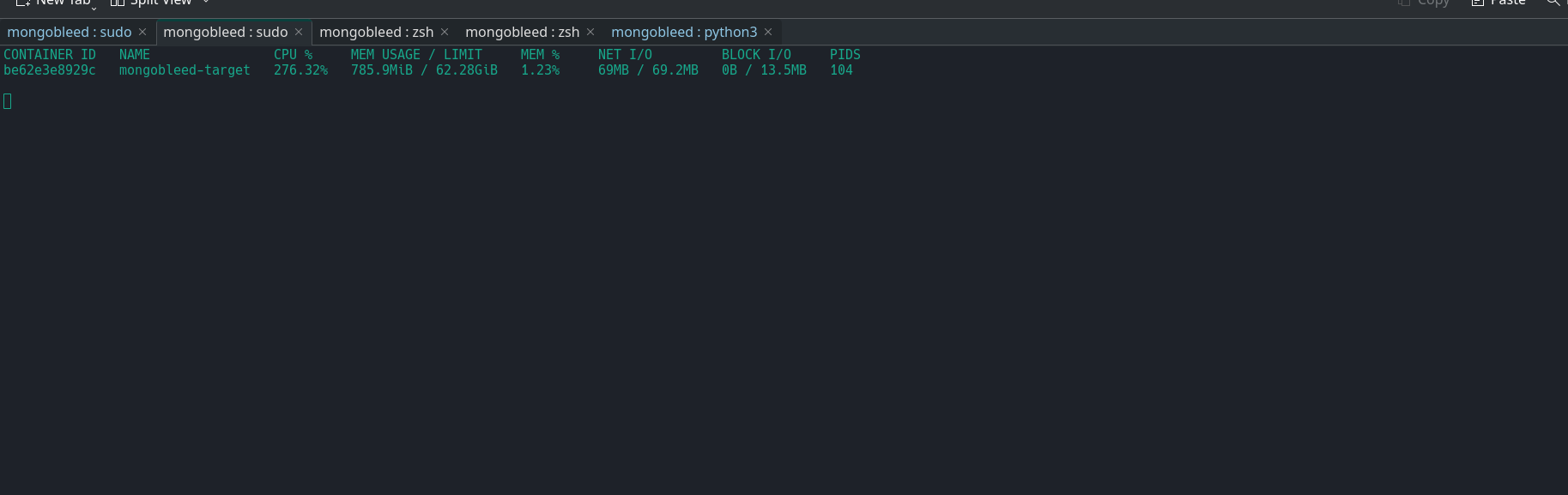
Next checking was done over network layer:
During exploitation there was about 10k and more request to mongodb
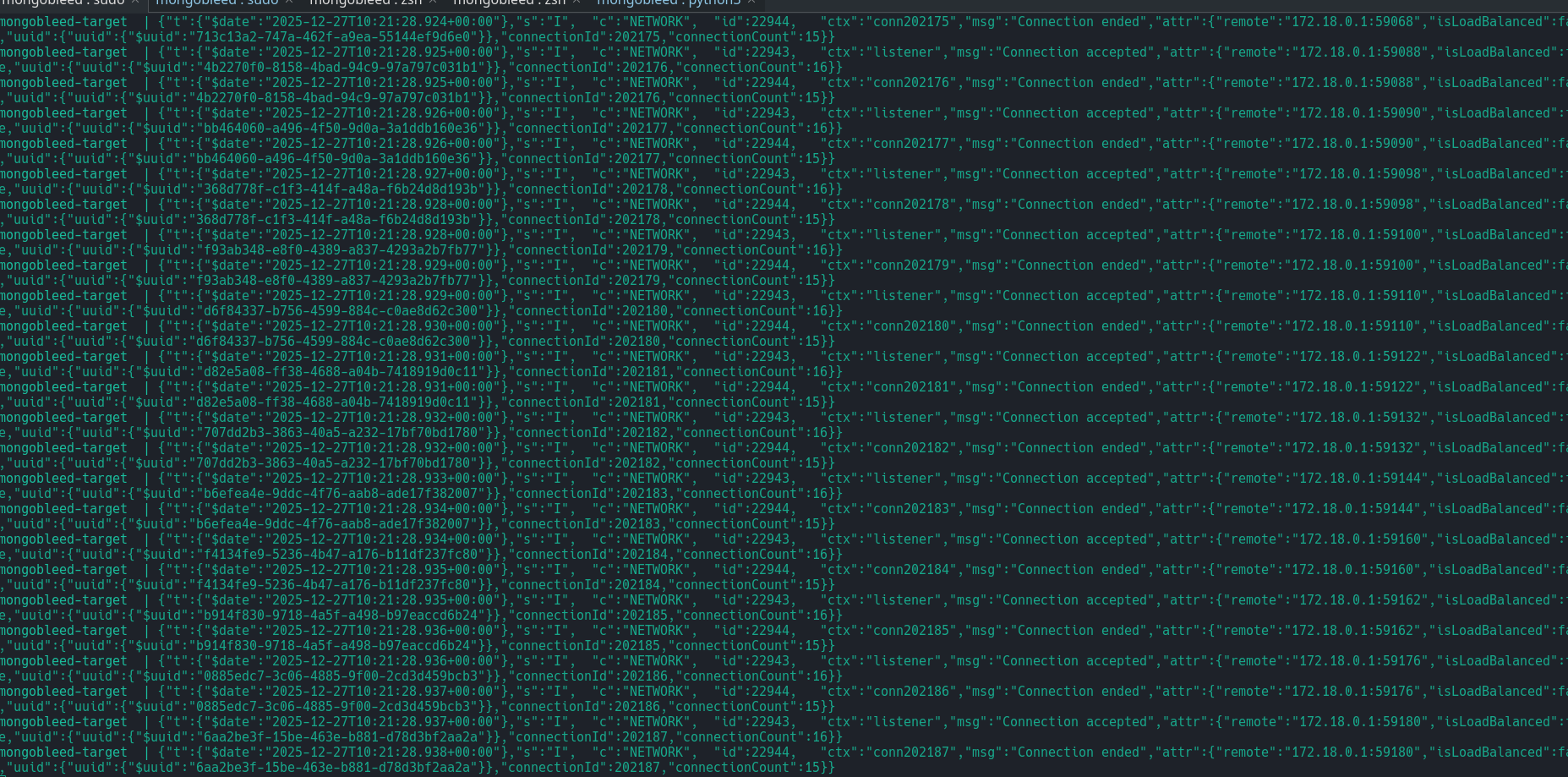
By analyzing these two metrics, I have concluded that abuse of this CVE can be detected in two ways. Of course, this depends on your database architecture.
- We can analyze historical spikes in CPU usage.
- If the number of connections from a single IP, previously unknown IP address increases to 10,000 or more, this anomaly should be investigated. However, this approach also depends on your specific architecture.
Conclusion: During certain hours, exploitation of this CVE may increase, but it’s important to keep in mind that triaging memory reads on the server is not an easy task even after successful exploitation.
