Agentic AI challenges in IDE: Forensic and extraction of traces PART 2
Background: As we continue our research around agentic IDEs which can leave traces, because at some IR stages you need to deal with such things—especially when an engineer's machine was involved in an incident. Let's deep dive into antigravity IDE AI agentic traces.
Shell execution traces:
Based on deep checking, the noted IDE under the hood is leveraging VS Code, and as a result of agentic work, it is always leveraging the path and filename "script/shellintegration.ps1". This means that we can craft our own detection to find such traces.
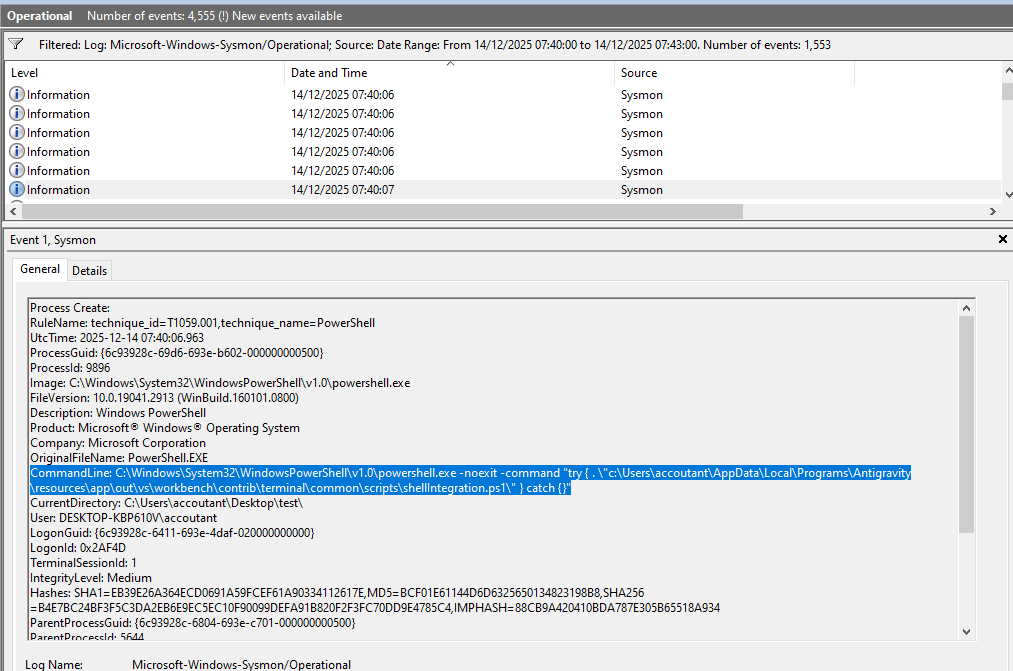
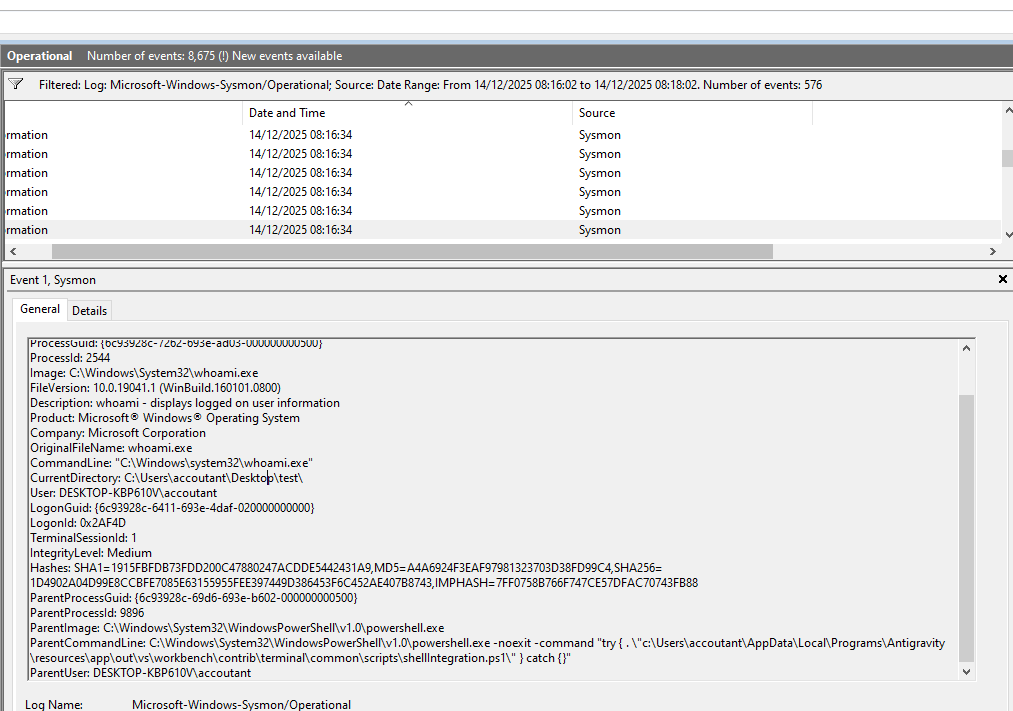
Agentic code generation:
During interaction with a file where code needs to be added, it creates a shadow copy of the file in C:/Users/YOURUSERNAME/.gemini/antigravity/codetracker/active (in the case where Gemini LLM was used) and in C:/Users/YOURUSERNAME/AppData/Roaming/Antigravity/User/History/RANDOMNUMBER
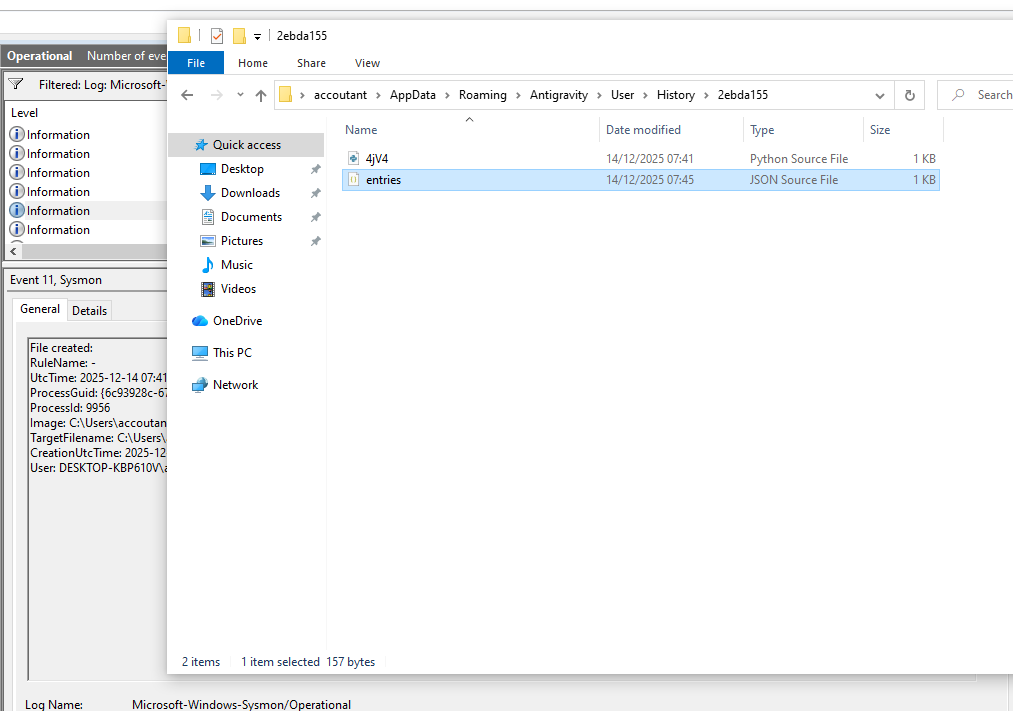
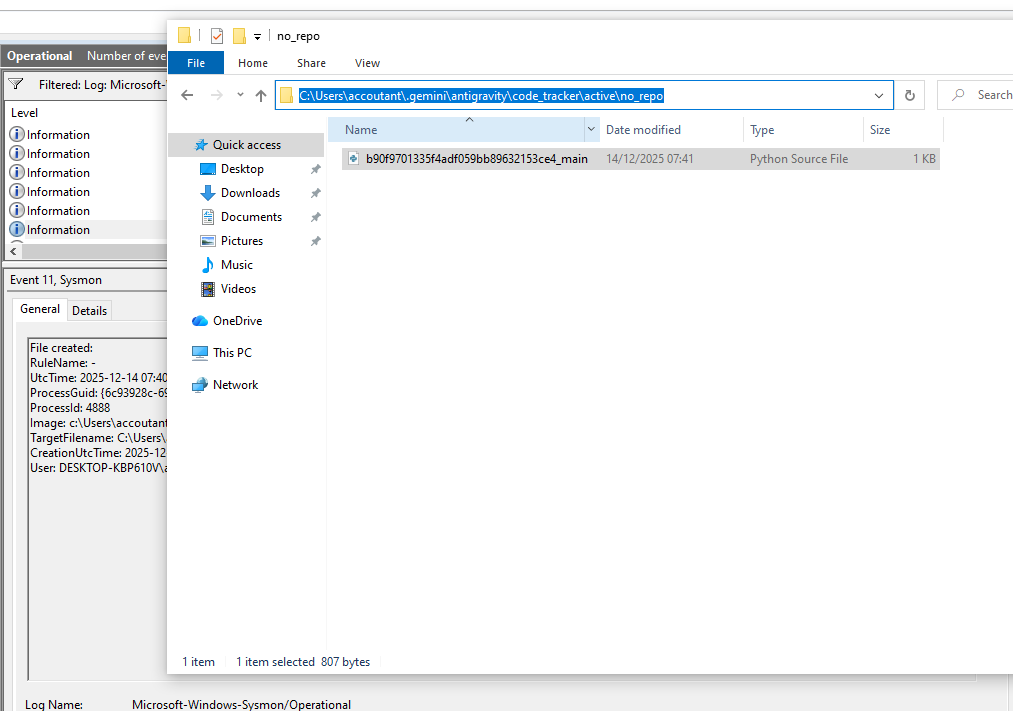
Conclusion: Using these methodologies, in the case of a machine infection, we can understand the possible impact related to the generated code where the engineer was working. Because I predict that, sometime later, infostealers will also look at those locations.
