Identifying the Root Cause of Cybersecurity Incidents Involving Exploit Detonation on Windows Machines
Background: During the incident response stage of "Log Collection," it is highly valuable to collect comprehensive data from the servers, especially when the affected system is running Windows OS. This is crucial because, as outlined in the MITRE ATT&CK framework, there are techniques where attackers exploit vulnerabilities (CVE) in installed software on the system. By collecting information about the installed applications and Windows updates, which may be responsible for such exploits, we can strengthen our analysis and better understand the root cause of the attack.
Technical Implementation: To achieve this, we need to divide our implementation into three components: - A centralized database needs to be hosted in a remote location. This database will store all relevant data retrieved from the Microsoft official page (MSRC Update Guide) using APIs, PowerShell scripts, or RSS feeds. - A PowerShell script must be developed to run on impacted assets. This script will gather information about installed software and cumulative updates. The collected data should then be sent to the centralized server for further processing. - The collected data from the assets will be correlated with the information stored in the database. Based on this correlation, the results will be shared via any designated communication channels.
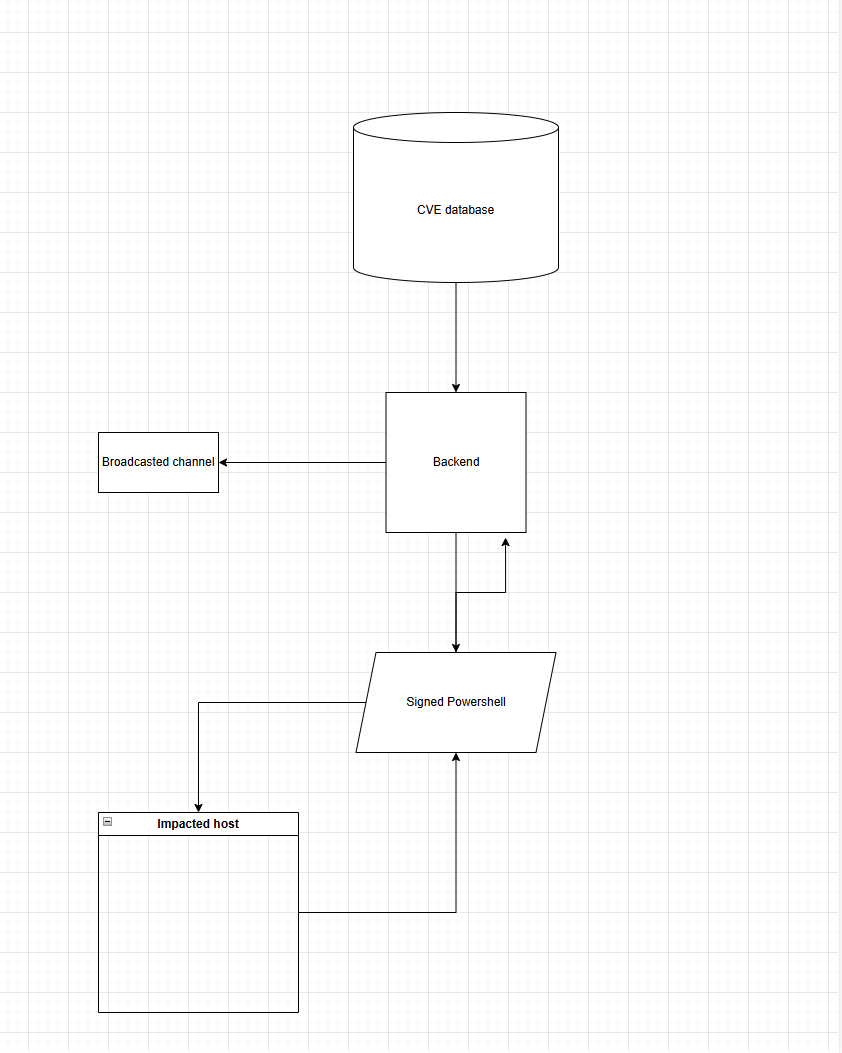
Conclusion and notes: During incidents, running untested or prebuilt solutions is not a good idea, as it may cause business disruptions and other issues. For this reason, as Incident Response (IR) specialists, we need to leverage built-in components provided by the Windows operating system to stay aligned with its ecosystem.
Additionally, before running any PowerShell script, we must ensure that the script is signed. This is crucial because Windows has protection mechanisms in place that require signed scripts for security purposes.
Stay Safe ! J0k3R !
