AI-Powered Polymorphic Phishing Pages: Detection Methods and Defensive Strategies
Background: As AI technologies rapidly advance, it is essential for us as cybersecurity specialists to understand how we can defend against emerging threats. One scenario that comes to mind is the possibility of threat actors using polymorphic phishing pages—where, for every user request, AI generates a new page with a unique layout and indicators of compromise (IOC).
Before diving into strategies to combat this, let's first clarify how we currently discover such phishing pages when our organizations are targeted by phishing attacks.
Specialized services are available that store the HTML structure of web pages in a historical view, monitor the resolution of certain domains, track JA3 fingerprints, and more.
Instead of relying on JA3 fingerprints and network-related IOCs, it may become nearly impossible to detect phishing campaigns against us in the near future.
Possible flow which can be used by threat actor to generate new structure of fake page .
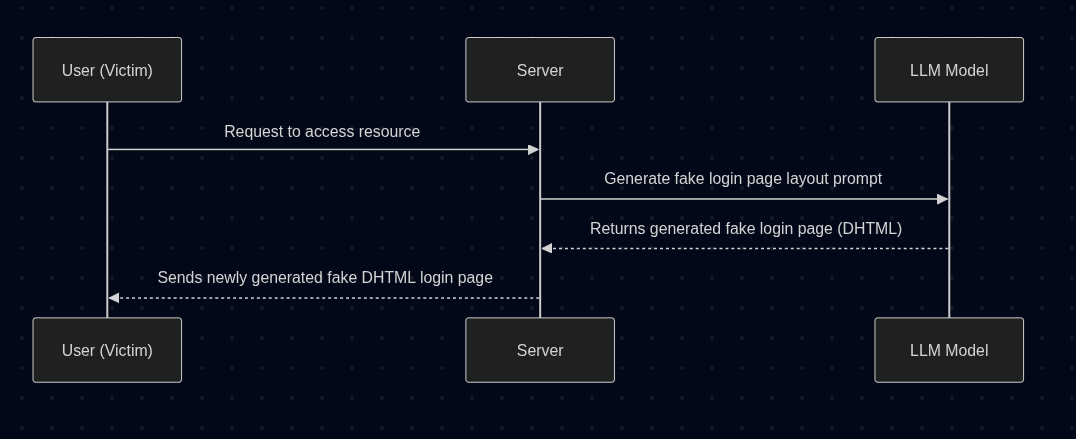
Detection Strategies:
- Implement special extensions which can detect AI written codes . But in this strategies you should be very careful with privacy related issues .
- Train your staff to detect phishing pages and to report about anomaly pages .
- Implement zero trust network which will block all risky domains and domains which risk is high or even medium
- Implement MFA in connection with risky users engine where you are capable to do it .
Conclusion: Soon, threats arising from AI will increase, and we must be prepared to face such challenges. One of the best methods to defend against these attacks is to strengthen your staff’s phishing resilience.
