Inside the Attack: How Smishing Campaigns Are Evolving with Covert Data Theft Methods
Background: Recently, there has been a noticeable increase in attacks carried out by fraudsters. These attackers use various delivery methods, ranging from social media platforms to SMS messages and iMessage. In this article, we will examine a specific example involving a phishing kit targeting credit cards. However, it also introduced a new idea for data exfiltration — one that not all specialists had previously considered.
Delivery method:
Attackers using compromised emails to deliver the message or using SMS system to deliver email with text . That you have some message .
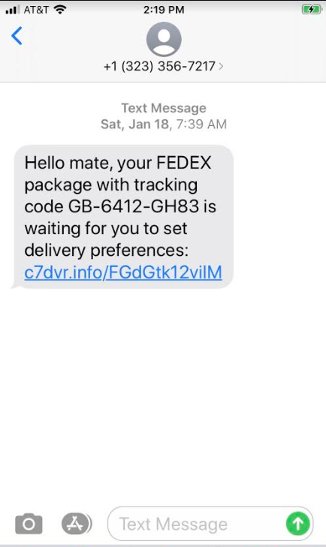
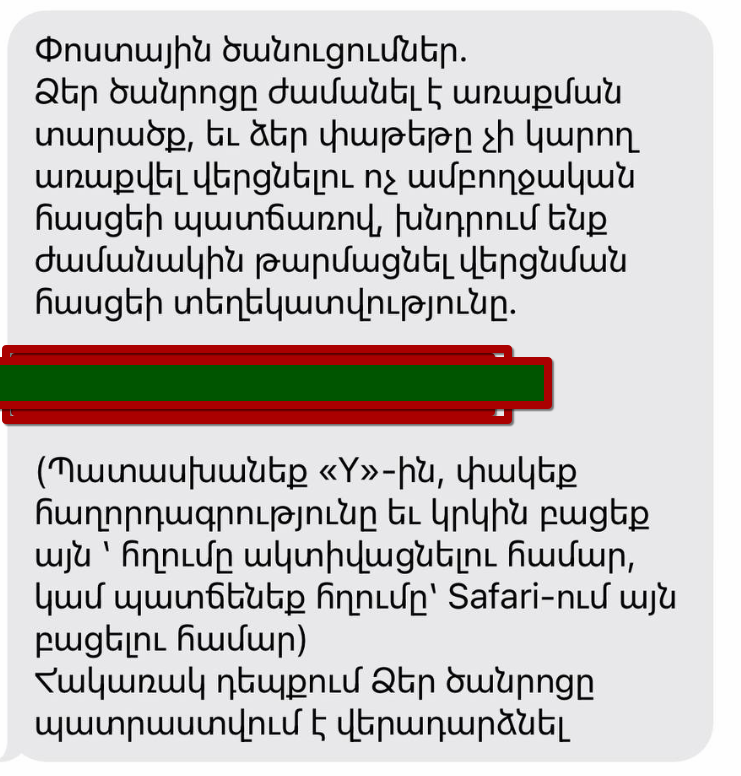
The next step requires you to visit the site using a mobile device. On the backend, it checks the User-Agent header to determine if the request is coming from a mobile device. If it's not, it won't redirect you to the intended page.
Exfiltration: Previously, attackers captured the form values after submission, but now they have adopted new technology that allows them to capture your live typing in real time using Socket.IO.

Conclusion: The technique of keystroke catching, which was introduced in recent attacks, is a new type of attack. Over time, it can evolve and become more sophisticated, particularly in its use in phishing attacks. Depending on the threat actor, it can be used to collect possible keywords, which may then be leveraged to organize brute-force attacks against organizational users.
Happy Hunt ! Joker !
