Mitigating the Risk: CVE-2024-39929 and Securing Exim Servers
Background:
Exim is a mail transfer agent designed for Unix-like systems, providing flexible capabilities for managing your own email server. It serves as the entry point for email communication within your environment, handling all internal and external email communications.
Like other similar solutions, Exim includes ACL (Access Control List) rules for managing MIME types. MIME types are used to identify the file type of an attached file, such as ZIP, VBS, EXE, DOC, and others. By utilizing ACLs, users can control and manage the allowed incoming attachment file types and related actions based on specific code abstractions.
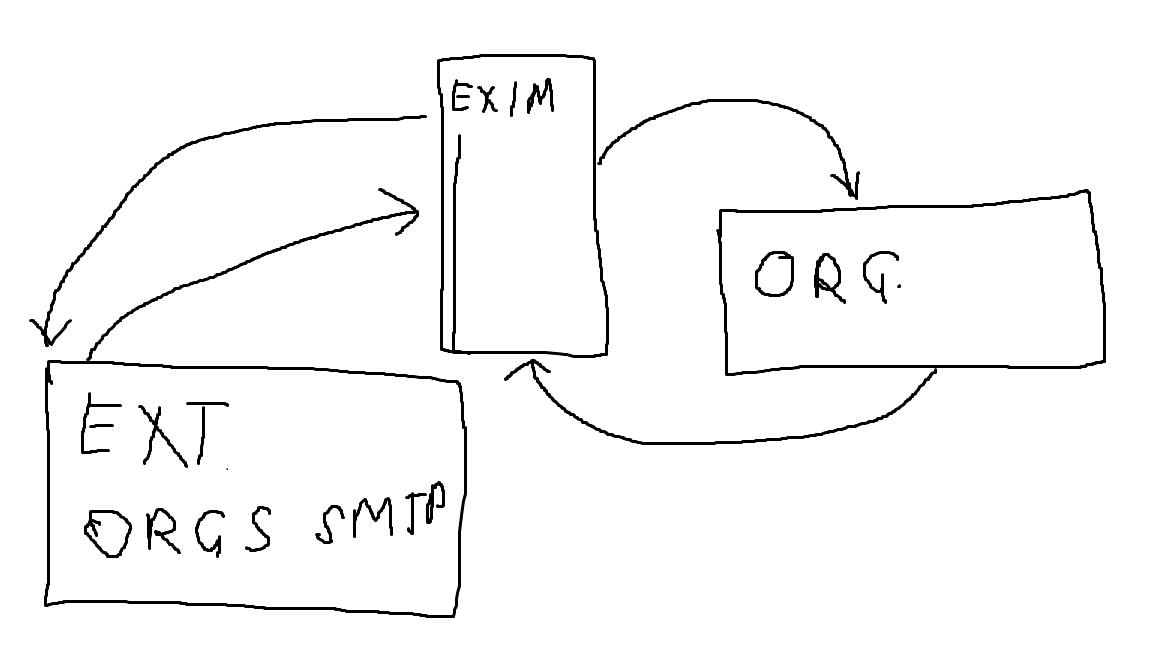
Issue: Even with strict ACL rules for MIME types in place, there are potential vulnerabilities that could allow bypassing such restrictions. CVE-2024-39929 highlighted an issue where the code was unable to properly handle multi-line MIME types, potentially allowing for bypassing the ACL MIME type restrictions. This vulnerability could potentially enable the attachment of files such as VBS or EXE despite the established restrictions. Exim Vulnerability Discussion
UseCases: Attackers often attempt to evade detection by concealing their payloads behind URLs, .LNK files, DOC files, or archives. However, a vulnerability like CVE-2024-39929 could be leveraged in scenarios where an organization has strict rules for external network connections. In such cases, the vulnerability could potentially be exploited to deliver a direct payload or loader into systems through email attachments, bypassing external network restrictions.
Mitigation: 1. It is crucial to update your EXIM servers to version 4.98, as lower versions are impacted by this CVE. Keeping your servers up to date with the latest security patches is essential for maintaining a secure environment. 2. Implementing email protection with defense-in-depth features is highly recommended. This approach involves using multiple layers of security controls to safeguard against email-based threats, such as phishing, malware, and spam. By deploying a combination of technologies and strategies, including anti-malware scanning, email encryption, spam filtering, and user authentication, you can strengthen your organization's defenses against email-borne attacks.
Current Threat Landscape against AM: There are about 100 or more hosts in the AM segment that may be using a vulnerable version of the Exim Server, it is important to assess whether they are utilizing this server as the primary email delivery transport. Understanding the extent of usage will help in prioritizing the update process and implementing necessary security measures.
Conclusion: This is a classic email protection threat that we deal with on a daily basis. One of the best practices is to continually train your staff through phishing attack simulations. It's also important to conduct daily threat hunting within your environment and establish a dedicated channel through which staff can report suspicious emails for further investigation.
When it comes to updating products, it's crucial not to rush the process. Testing new versions before deploying them into production is essential. This helps to identify deprecated features, harmful code, and other potential issues that could impact your business environment.
