The danger of leaked hash password from the perspective of defense in depth
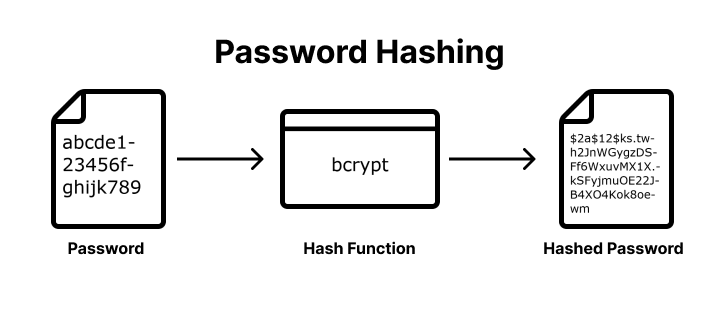
Background: Before delving into the scope of leaked hashed passwords, it's important to understand the purpose of hashing. At a high level, hashing is a one-way function that transforms any input value into a fixed-size string of characters, known as a hash value or digest. For example, the string "admin_super_password" can be transformed into "6434b00d725cab577e0b3b5067f6d9a7447fe46e7a7a2fcd40d32720ac10bc11" using a hashing function.
In the context of password security, when a user sets or enters their password, a middleware function hashes the plaintext password into a hash value. This hashed value is then stored in the database. When the user tries to log in subsequently, the middleware again hashes the entered password and compares this hash with the stored hash in the database. If they match, access is granted to the system or application environment.
Chapter 1: Data Breach and Initial Stage of Attack T592 - Gathering Victim Identity Information and Other MITRE Stages for Information Gathering :
We've seen numerous instances where major platforms handling large customer databases have fallen victim to data breaches. In these breaches, hashed versions of user passwords, along with other sensitive information, become accessible on specialized platforms. Threat actors leverage tools like Have I Been Pwned and others to aggregate this leaked data, gaining access to hashed passwords. Using sophisticated techniques, they may acquire email addresses and additional details through B2B platforms. By cross-referencing this information with databases from services like Have I Been Pwned, they can identify breaches where the hashed passwords were exposed, potentially leading to unauthorized access.

Chapter 2: Impact to your environment from third arty databreach - Password spraying attack against your organization : In recent times, advancements in hardware and computing capabilities have made it possible to crack even older leaked passwords and transform them back into plaintext. This has made it crucial for threat actors to constantly attempt to crack hashed passwords. They exploit a common human psychology where individuals often reuse password patterns across work and personal accounts. This vulnerability allows them to launch password spraying attacks against business platforms, hoping to find matches and gain unauthorized access.
Mitigations:
- Subscribe to services like haveIbBeenPwnd and in a case of notification from there always checked if passwords hash was leaked . If yes then change current password for the user . And never use the same pattern anymore .
- Monitor your environment in case failed login where you do not have employees or where was involved any proxy IP
- If applicable monitor privilege escalation activity in environment from non authorized user
My conclusion: Hashing serves as a critical security measure because even if the hashed values are exposed, such as during a data breach, it remains extremely challenging to reverse-engineer the original plaintext password from the hash. This cryptographic process significantly enhances security by safeguarding user credentials, thereby mitigating the risk of unauthorized access to the database.
However, it's important to remain vigilant even if only hashed passwords were leaked from third-party platforms. Any unauthorized access poses a risk that can impact your brand reputation and compromise your environment. Therefore, proactive security measures and monitoring are essential to protect against potential threats and maintain trust with your users.