Part5: Kernel protection preventive mechanisms in Linux systems and methods for monitoring them (Lockdown Mode)
Background: The Linux kernel lockdown mode was introduced in Linux kernel version 5.4. Its purpose is to help protect the kernel from actions that could compromise the confidentiality or integrity of the system. Lockdown mode restricts certain kernel features and operations that could be exploited by attackers or could allow unauthorized access to sensitive information.
The implementation of lockdown mode is managed by the kernel function named lockdown, which can be found in the kernel source (for example, in security/lockdown/lockdown.c).
To check the current status of kernel lockdown mode, you can use the following command in your terminal:
cat /sys/kernel/security/lockdown
The output will show the current lockdown mode, such as integrity, confidentiality, or none.

If the string “none” appears in brackets, it means that lockdown mode is not enforced. If “integrity” is shown in brackets, it indicates that the system kernel is protected from unauthorized modifications. If “confidentiality” is displayed in brackets, it means the kernel is attempting to prevent data access or leaks through debugging components. Note that enabling confidentiality mode may cause certain EDR/XDR solutions to malfunction.
Side effect:
After setting the kernel lockdown mode to “integrity,” the system cannot revert to a different mode.
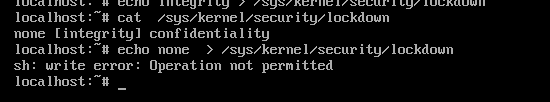
Threat actors can use the same technique to block XDR/EDR solutions from accessing log collection if they manage to gain access to your system.
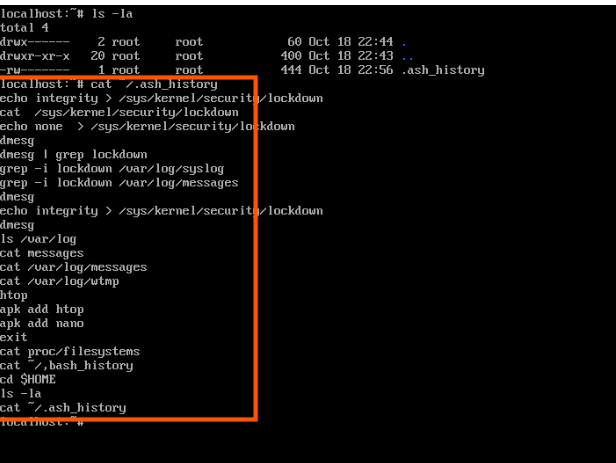
Detection way: One method of detection is to check dmesg, although it may not always show who attempted to abuse the capability. However, you can confirm if lockdown mode has been activated. Another way is to collect Bash history to look for interactions with that setting.
Conclusion: This feature needs to be reviewed very carefully before being applied to production. In my opinion, the noted capability should be implemented into your CI/CD pipeline.