T1590.001: Exposed Domain Registration Records – A Tool for Both Threat Actors and Cyber Defenders
Background: Before coming across this shared article, I noticed an interesting correlation: sometimes, domain registrar customers forget to enable email privacy. Once this oversight is discovered, they quickly take steps to hide the record. As a result, both threat actors and researchers can exploit this process to uncover the individuals behind a domain. Consequently, an organization may be targeted based on this record, or the threat actor orchestrating an attack behind the domain may be exposed.
How this gap working ? During domain registration, a customer may forget to enable email privacy because, by default, the domain registrar service may have it turned off. As a result, when the domain propagates over DNS relays, this information is first scraped by Threat Intelligence (TI) platforms. Until the threat actor (TA) or organization takes steps to hide this data, it remains exposed. In any case, the information has already been leaked.
Automation flow: In our automation, we need to address two scenarios:
- Identify domains where the assigned registrar email contains the domain name.
- Identify domains where the registrar email does not contain the domain name.
As a best practice, we should use a Threat Intelligence (TI) platform to automate this process.
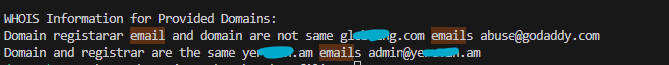
In the above case, you will notice that in one scenario, the assigned registrar email does not match the domain name but is associated with a legitimate registrar domain. In the second scenario, the domain and the assigned registrar email domain are the same. This means that for the second scenario, I can use this data to establish correlations in case of a weak point. Additionally, there is a third scenario where the domain is registered to a Gmail.com personal email, which creates a larger attack footprint due to the exposure of this information.
Conclusion: Always ensure that before registering a domain, you haven't left any traces behind. Threat actors can use this information for T1590.001 to identify weaknesses, which could become critical vulnerabilities for your organization.
- When registering a domain, avoid publicly associating your email address with it if possible.
- Use private registration services to protect your personal details (e.g., WHOIS data).
- Ensure that your email is not publicly visible on the website or in the domain registration details to reduce the risk of targeted attacks.
- After exposing email address replace it with new one and never use it .
