Part4: Kernel protection preventive mechanisms in Linux systems and methods for monitoring them (SLUB)
Background: As we continue our journey into the mechanisms of kernel protection toolsets and monitoring, let's focus on our next candidate: SLUB.
In simple terms, SLUB (the Unqueued Slab Allocator) is the Linux kernel's default memory allocator for managing small memory objects used inside the kernel. It acts like a smart organizer, maintaining caches of frequently used objects so they are readily available for quick access.
SLUB protection mechanisms: SLUB includes debugging features such as poisoning and red zones to detect and prevent use-after-free and memory corruption errors early. These two features help protect the kernel from both intentional and unintentional threats.
Red zones are guard zones placed around SLUB objects. They get filled with specific marker values . Any modification to these marker values indicates an out-of-bounds (OOB) memory access or corruption. The system detects this upon next memory access and reports the issue.
Poisoning involves filling objects with special poison values after they are freed. When a previously freed object is reallocated, SLUB checks if these poison values remain intact. If not, it flags a use-after-free error. The detection happens at reallocation time, helping identify "Use after free"(UAF) bugs.
Enable SLUB protection: By default, not all Linux distributions enable this feature. To enable it, edit your GRUB configuration file and add slub_debug=FZPU to the GRUB_CMDLINE_LINUX_DEFAULT line.
Z stands for Redzone detection (detects buffer overflows). F stands for Free objects check (detects double free and invalid free). P stands for Object poisoning (detects use-after-free bugs). U stands for User tracking (tracks the user/process responsible for allocation/free). After saving the file, update GRUB and reboot your system for the changes to take effect.
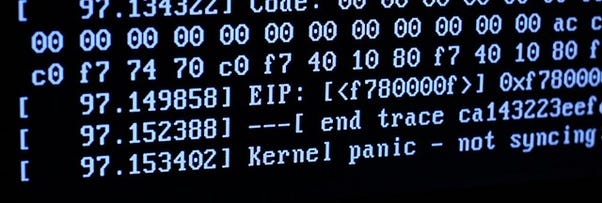
Example of activated SLUB mechanism

Detection method: Always check for keywords such as "BUG", "Redzone", "object", "Slab", and "SLUB" in logs, which can be found in dmesg, /var/log, and similar locations.
Conclusion SLUB’s protection features, such as red zones and poisoning, significantly improve the detection of memory corruption and use-after-free errors in the Linux kernel. By enabling these mechanisms, administrators can proactively identify and mitigate both accidental and intentional threats, strengthening kernel security and system stability. Regular log monitoring remains important for early detection and response to such issues.