Defending Against ClickFix and FakeCaptcha: Detection Techniques for Modern Malware Campaigns
Background: ClickFix or FakeCaptcha attacks have become a common component of many attack campaigns. These techniques enable threat actors, with the user's unwitting assistance, to execute arbitrary processes under the current user's context. By leveraging JavaScript capabilities and various evasion techniques, attackers can effectively bypass security measures and gain control over targeted systems. Based on my research, I have identified effective methods to combat this threat by detecting it at the pre-execution stage.
Attack in a core: When a user navigates to a compromised page, the attack attempts to manipulate legitimate JavaScript capabilities to inject malicious text into the user's clipboard. In some cases, before this injection occurs, the threat actor's JavaScript may also exfiltrate metadata about the user—such as geolocation information—to a Telegram channel.
After the clipboard has been modified, the attack instructs the user to press Win+R, which opens the Run dialog, and then use Ctrl+V to paste the previously injected text, followed by pressing Enter. If the victim complies, this sequence executes the malicious code.
The injected command leverages "Living off the Land" techniques, using built-in system utilities to communicate with the attacker's server, download additional malware, and execute it. This can ultimately result in various types of threats being deployed on the system, ranging from remote access trojans (RATs) to infostealers.
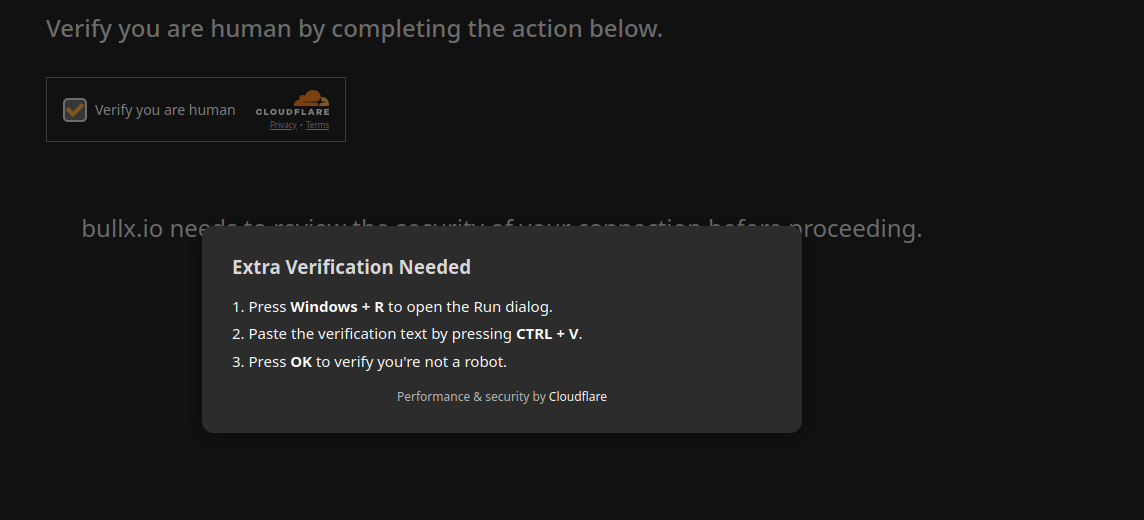
Detection Direction: During research into the various commands leveraged by threat actors in JavaScript code, I observed that threat actors often use techniques and functions to inject harmful code into the clipboard. By monitoring for these patterns, we can detect such malicious strings with a high degree of confidence when a user navigates to a page.
Detection Tool: For detection purposes, I used a simple browser extension capability that allows reading all the content of the page and shows a notification when suspicious JavaScript code is detected. At its core, the implementation is based on manifest v2 of browser extensions. An example of such an extension can be found on the GitHub page.
Sleeping gorgon project link: https://github.com/lisajan-hash/sleeping_gorgon
Conclusion: Of course, we should not always rely on a single detection method, because over time JavaScript code can be obfuscated and attack techniques can change. For this reason, there are some recommendations that every organization should follow:
Always use XDR solutions on machines. Use IDS/IPS systems. Never allow users to have local administrator privileges on their machines. Do not allow users to execute any files or components that are not required for their job responsibilities.
Happy Hunt ! J0k3r !
