Navigating Incident Response When Logs Are Missing
Background: In incident response log collection, you might encounter situations where EDR/XDR solutions or log collectors are not present on a machine. Additionally, some syslogs might be missing. However, this does not mean you should stop investigating the threat actor's activities, as these steps are crucial for organizing the initial response or analyzing the threat actor's actions.
Method:
Before diving into the challenge, it's important to understand that, at certain stages, a threat actor's actions can persist on a system even after the machine is restarted. With that in mind, we can determine where to investigate and what metadata to examine. And what if I told you that the answer is quite close and right in front of our eyes?

The thing:
Let's conduct a small test on a Linux machine, simulating a threat actor who wants to create a new user on the system.
Take the date

We see that date is Apr. 25 16:16:37 UTC
Now add new user from the perspective of threat actor with the name evil_account
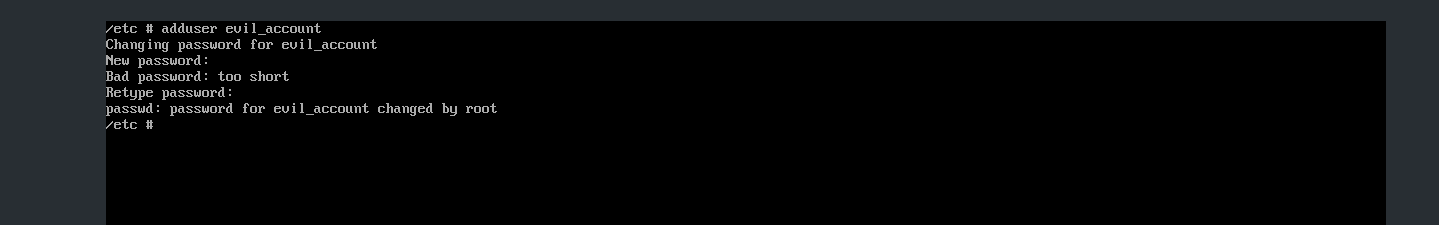 Now get current time
Now get current time
Now what ?
Navigate to /etc and type ls -la and take a look to change time
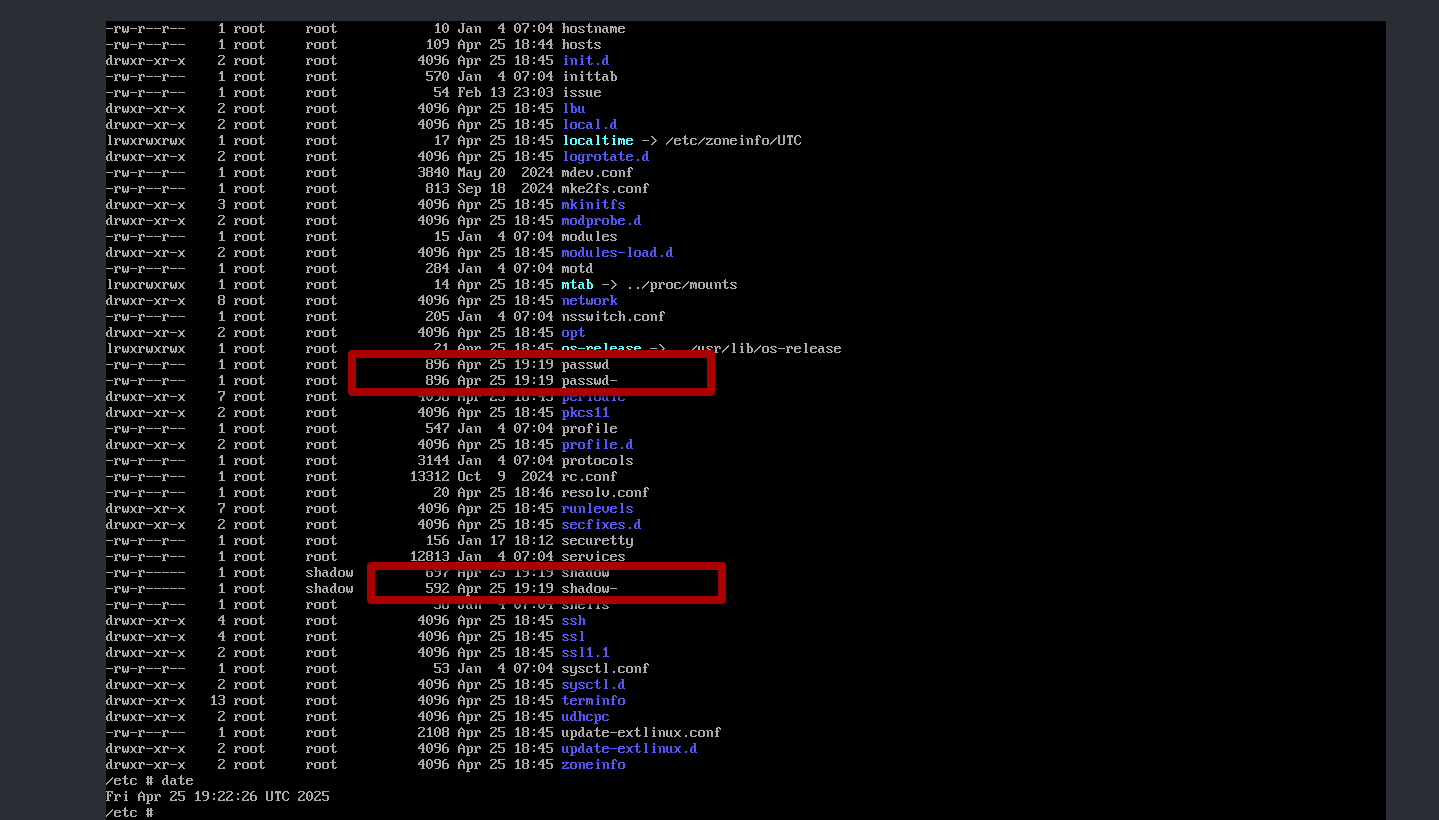
Because we added a new user as an additional backdoor to our system, we can observe that the file modification time was set to the time when the activity was executed. This timestamp will remain the same until the next modification by threat actor.
Now what ? As Incident Responders, we should always be prepared for such situations. It is essential to have in-house scripts that can detect and alert us about suspicious anomalies, even in cases where logging is not in place. While it is true that such modifications can potentially be tampered with, not all threat actors possess the skills required to thoroughly clean up traces behind them.
Conclusion: The above example is not the only one that leaves persistence on a system in the wild; there are multiple TTPs (Tactics, Techniques, and Procedures) that leave similar traces. As defense specialists, it is crucial for us to understand and assess all such changes and traces.
Happy Hunt ! J0k3r
