Technical Detection of Typo-Squatted Campaigns: A Case Study on Roblox Game Account Hijacking
Background: A few days ago, UNIT42 reported tracking an active phishing campaign targeting Roblox game players, which is hugely popular worldwide. In a previous article, I covered the broader threats posed by typosquatted domains at a high level. Now, by combining this real-world case with my earlier analysis, we need to explore how to effectively combat this threat and what technical measures should be implemented to detect and mitigate such attacks.
Methods to lookup: 1. Private methods 2. Typo domain list
Private Method: The attacker made some mistakes, which led to the creation of unique values across various assets used in the campaign. As a result, it was discovered that the domains were linked to a page containing instructions on how to steal gamer accounts.
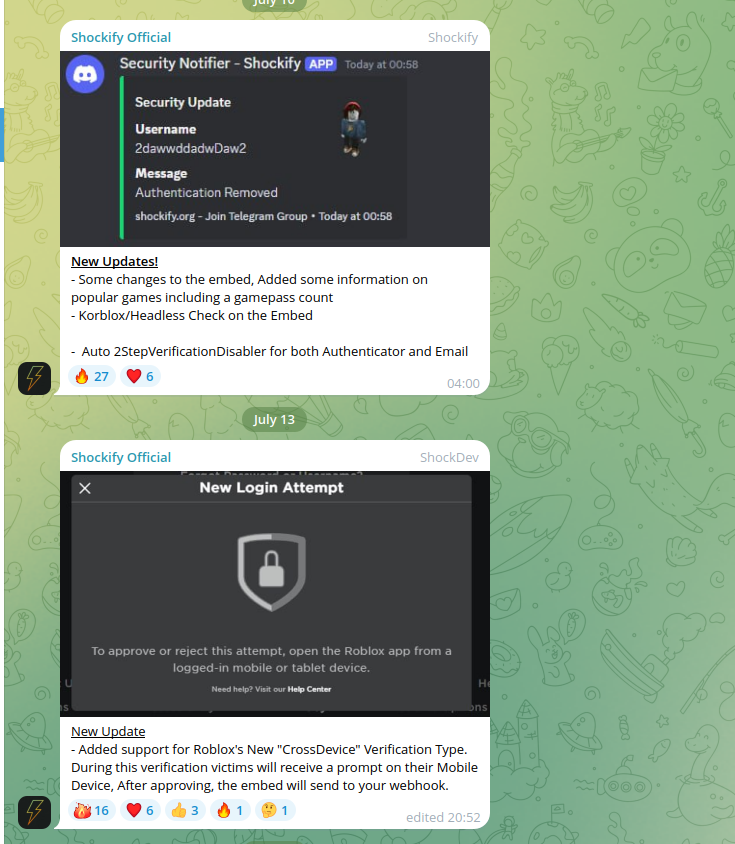
Typo domain list: For the typo-related domain list, I created a simple script [ LINK ] that pulls all TLD data from IANA's root database. The script then concatenates this data with the domain that needs to be checked, generating permutations for TLDs, MX, NS, and other domain records. It subsequently makes requests to each generated domain and checks for a successful status code response.
Conclusion: This case study demonstrates that at any given time, domains can appear that may be used to bypass the perimeter you're protecting. The purpose of this article is twofold: first, to share a script that you can run on your domain to generate permutations and identify unknown TLDs associated with it; and second, to highlight the importance of proactively monitoring and securing your domains. In this case, the attack targeted a gaming platform, but in other scenarios, such attacks could affect business-critical, government-related, or other high-value domains. It's crucial to always stay vigilant and protect your digital assets from such threats.
Happy Hunt, Jok3r
